Dllhost.exe spawning multiple instances may seem suspicious but it is not necessarily a virus. Dllhost.exe is a wrapper application that is part of Windows 7 and can be used to run DLL files as applications and running some DLL’s as threads can be legit windows system activity. Last week, however, I had a workstation exhibiting extremely slow performance and an ever growing number of dllhost process instances which when killed re-spawned within seconds. A Trojan named poweliks was to blame (see process explorer screenshot below). If you kill the top level dllhost.exe process tree, soon thereafter a conhost.exe process would fire an instance of power shell which would slowly start building up the dllhost.exe processes again. This was certainly suspicious behavior. Oddly enough neither McAfee nor Symantec (As of 11/2/14 Symantec.cloud is able to block commands issued to and from poweliks on an infected machine and sometimes detect the infection but it cannot remove it) are able to detect or remove the threat. After some research I found that the most likely culprit is a variant of poweliks file-less trojan. It works by residing only in the system memory (that’s why it is hard to detect) and it turns the system into a bot to be controlled by a remote attacker. It is typically launched via a unicode entry in the startup section of the HKCU registry and that is therefore impossible to detect using tools like autoruns (which will not display it). Once launched, the Trojan runs only in memory and uses legitimate windows processes to perform bot attacks or allow remote hacker control. The first thing it does when launched is to re-insert itself back into the HKCU start-up registry section, so removal is tricky and must be timed quickly.
[the problem]
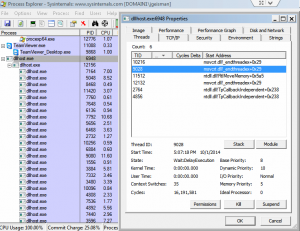
System performance slows to a crawl and when analyzed with Process Explorer or task manager, the process dllhost.exe appears to have gone haywire. See the example in [figure 1].
[figure 1]
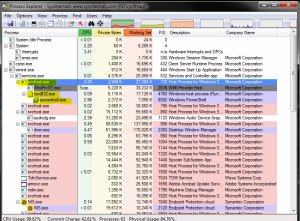
When the root dllhost.exe process tree is killed (terminated), it re-appears within seconds as part of svchost.exe [figure 2] and again starts slowly spawning an ever growing number of child dllhost.exe processes like shown in [figure 1].
[figure 2]
[the solution]
–UPDATE 11/11/14–
Symantec has posted a Poweliks removal tool which eliminates the need to follow the instructions below. The Poweliks tool has been tested and is capable of removing a poweliks infection. The tool and more information on how to use the tool can be found here:
http://www.symantec.com/security_response/writeup.jsp?docid=2014-111020-0511-99
[Direct download] Symantec Poweliks Removal tool for x64 bit versions of Windows
[Direct download] Symantec Poweliks Removal tool for x32 bit versions of Windows
One option is to backup, delete and restore/re-create the user profile for the user. I have not tested to see if using Windows Easy Transfer to backup and restore the user profile will successfully eliminate the Trojan. I have been able to successfully remove the Trojan by backing up all user profile related files with the exception of AppData, then re-creating the user profile and restoring those files.
If you are comfortable with Windows, this may be an easier/faster resolution:
Close all applications and save your work. Running these steps in the order below is necessary.Download and run Process Explorer as an administrator. Available here: http://technet.microsoft.com/en-us/sysinternals/bb896653.aspxDownload and run the latest version of RogueKiller. Available here: http://www.bleepingcomputer.com/download/roguekiller/.Let RogueKiller initialize and then click the Scan button. RogueKiller will automatically open the help page on how to remove Poweliks if it finds an infection or a thank you page for using RogueKiller if you’re using it for the first time. Close those windows if they pop up. Once the scan is complete, navigate to the Registry tab in RogueKiller [figure 3] and scroll to the bottom. You should see the a line item in red like the screenshot below [figure 2] if your system has been infected:
[figure 3]
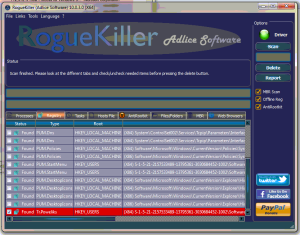
NOTE: RogueKiller is known to incorrectly identify malicious programs and hijacks on computers from time to time, so I recommend only checking the box next to the Poweliks infection before clicking Delete.
Get ready to hit DELETE in RogueKiller, BUT DON’T CLICK IT JUST YET.Using Process Explorer, scroll through your active process list and locate a varying number of dllhost processes as shown in [figure 1]. Right-click the root process and select Kill Process Tree. YOU’LL SEE A PROMPT ASKING IF YOU ARE SURE YOU WANT TO KILL THE SELECTED PROCESS TREE, click YES.Now click DELETE in RogueKiller and reboot the system immediately. It is important to reboot the system before the Trojan re-launches and puts itself back into the registry. NOTE: This Trojan also runs in Safe-Mode with networking.In some cases the Trojan can be responsible for creating a large amount of data in C:\users\<username>\appdata\local\temp\. I recommend removing this data with CCleaner available here: https://www.piriform.com/ccleaner/builds
That’s it.